Librehosting » Historique » Révision 15
Révision 14 (sacha, 02/08/2018 00:44) → Révision 15/44 (sacha, 02/08/2018 01:24)
# Configuration of a Libre Hosting aka Anouncing our public IPs to Internet from an indifferent places technical resume: IPSec between OPNSense and OpenBSD to announce our ASN IP from an indifferent ISP place. ## General presentation ### Who we are Aquilenet is a non profit organization since 2010 and a "do it yourself ISP", member of a Federation of similar ISP in France called [FFDN](https://www.ffdn.org). We are netneutrality builders, helping for more freedom and building networks using and participating Libre Software. We provide xDSL, VPN and we hope soon Fiber accesses, and a lot of services for our members (mail, nextcloud, hosting, VPS...) and for others [searx](https://searx.aquilenet.fr), [Etherpad](https://pad.aquilenet.fr), [Pastebin](https://pastebin.aquilenet.fr), [Peertube](https://tube.aquilenet.fr), ... ### The need: create a Libre format hosting in our cool local called "la mezzanine". To allow our the members of our non-profit organization to connect the hardware they want (like Nuc, Raspberry pi, tower, etc...) in our Libre hosting space called "la mezzanine" with a Public IPv6 and IPv4 and from our [ASN](https://en.wikipedia.org/wiki/Autonomous_system_(Internet)), we need to announce our IPs from another place than our Datacenter. ### How we do We have to tunnel all the network from the Libre Hosting to Internet and vice versa. We have tried first with OpenVPN but the userland application use to much resources for needed bandwidth (200Mbps). This IP range will be routed by IPSec to our ASN point of BGP announce in our datacenter, then they will route them to the Libre Hosting. From our Libre Hosting we have a OPNSense Firewall and in our Datacenter two clustered [OpenBSD](https://www.openbsd.org/). A scheme to explain this: 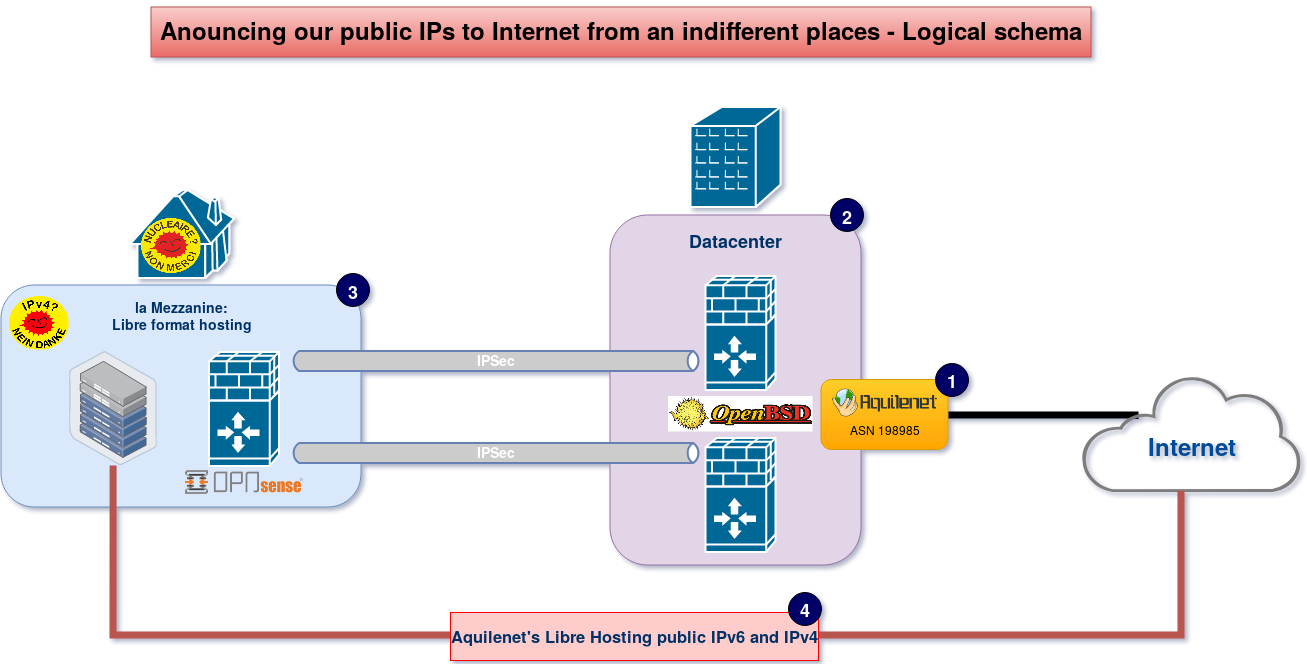 Scheme explanation: * (1) ASN & BGP With our ASN with can do BGP to announce our IP adresses in our Datacenter. * (2) Firewalls in the Datacenter The job is done with a cluster of firewalls using the magic power of [OpenBSD](https://www.openbsd.org/) and [OpenBGPD](http://www.openbgpd.org/). For firewall Redundancy we use [CARP and pfsync](https://www.openbsd.org/faq/pf/carp.html) * (3) La Mezzanine Is our cool place where we can meet our members and friends. This place use green power with an alternate electricity supplier, called [Enercoop](https://en.wikipedia.org/wiki/Enercoop) is a French electric utility cooperative company, which only uses renewable energy. Here, the firewall is [OPNSense](https://opnsense.org/) doing the PPPOE connection on a general public fiber provider (Yes we had to hack a little to remove this ISP baclkbox). * (4) Public IPv6 and v4 from the Mezzanine to Internet This firewall is routing threw an IPSec tunnel (for each OpenBSD firewall) our public dedicated IP for this place. These IP allow our friend's to put there their servers servers / Arduino's & co to Internet with our network <3 --- ## Technical information, let's rock ! ### [OpenBSD](https://www.openbsd.org/) configuration We configure the [OpenBSD](https://www.openbsd.org/)'s IPSec configuration file for 2 Phase 2 tunnels one for IPv4 another on for IPv6 **/etc/ipsec.conf** /etc/ipsec.conf ~~~ ike passive esp from any to $LIBRE_HOSTING_PUB_IP_V4/26 \ peer $OPSense_Public_IP\ main group modp2048\ psk "mysupersecurepass" flow esp from any to $LIBRE_HOSTING_PUB_IP_V4/26 peer $OPSense_Public_IP flow esp from any to $LIBRE_HOSTING_PUB_IP_V6/48 peer $OPSense_Public_IP ~~~ ~~~ chmod 500 /etc/ipsec.conf ~~~ **Launch Launch the tunnel:** tunnel: ~~~ isakmpd -K ipsecctl -f /etc/ipsec.conf ~~~ To make it permanent add this to /etc/rc.conf.local: ~~~ isakmpd_flags="-K" ipsec_rules=/etc/ipsec.conf ipsec=YES ~~~ check the configuration: ~~~ ipsecctl -sa ~~~ Enable some logs on Isakmpd: ~~~ sh -c "echo S \> /var/run/isakmpd.fifo" less /var/run/isakmpd.result ~~~ and: ~~~ isakmpd -d -DA=70 -K ~~~ Check IPSec Flows: ~~~ ipsecctl -F ~~~ ## OPNSense configuration   ### \\-\> Configuration1: Performances - AES\_CBC\_256/HMAC\_SHA2\_512\_256/MODP\_8192 - Cerbere11 last pid: 45038; load averages: 0.27, 0.34, 0.31 up 0+00:56:47 19:07:15 49 processes: 1 running, 48 sleeping CPU 0: 3.9% user, 0.0% nice, 0.8% system, 3.1% interrupt, 92.1% idle CPU 1: 1.2% user, 0.0% nice, 0.0% system, 6.3% interrupt, 92.5% idle CPU 2: 0.4% user, 0.0% nice, 0.0% system, 21.3% interrupt, 78.3% idle CPU 3: 5.9% user, 0.0% nice, 0.0% system, 2.4% interrupt, 91.7% idle Mem: 109M Active, 145M Inact, 387M Wired, 152M Buf, 7214M Free - Cerbere1 load averages: 1.18, 0.95, 0.74 cerbere1.aquilenet.fr 19:08:23 43 processes: 1 starting, 40 idle, 1 dead, 1 on processor up 3 days, 18:40 up 3 days, 19:21 CPU0 states: 0.2% user, 0.0% nice, 2.8% system, 7.4% interrupt, 89.6% idle CPU1 states: 0.0% user, 0.0% nice, 22.4% system, 0.0% interrupt, 77.6% idle CPU2 states: 0.0% user, 0.0% nice, 20.2% system, 0.0% interrupt, 79.8% idle CPU3 states: 0.0% user, 0.0% nice, 10.8% system, 0.0% interrupt, 89.2% idle Memory: Real: 584M/2111M act/tot Free: 5793M Cache: 754M Swap: 0K/8405M - bande passante  ### MTU Linux: ping -M do -s 1172 185.233.102.130 =\> OK Linux: iperf3 -c 185.233.102.130 -M 1160 =\> OK Linux: ping -M do -s 1173 185.233.102.130 =\> NOK Linux: iperf3 -c 185.233.102.130 -M 1161 =\> NOK - netcat qui fait un echo socat TCP4-LISTEN:4444,fork EXEC:cat